Facial data belongs to citizen privacy data, which is unique and irreplaceable. The three major national regulations, including the Cybersecurity Law, Data Security Law, and Personal Information Security Standards, all involve management regulations for such data and privacy.
As a non-profit organization, schools provide higher quality services to teachers and students by building facial recognition applications throughout the campus. Therefore, in the process of applying facial recognition technology, it is necessary to strengthen the protection of personal privacy and the construction of data security.
Face recognition, as the most convenient, fast, and effective unique identity medium, has been applied in various scenarios of campus learning and life. However, the disorderly collection and construction of facial data in various applications have also occurred.
On this premise, schools need to build a unified platform with security capabilities based on facial data, enabling them to manage disorderly and chaotic collection of facial data in a unified manner, ensuring the security of facial data, and empowering various facial recognition business applications.
Unified facial platform solution
What are the issues?
1. Collection and interworking
Solve the problem of scattered collection of facial data in the initial stage and inability to achieve sharing and interoperability.
2. Ready to use on the ground
Solve the problem of difficult application implementation and inability to quickly provide convenient services to the school.
3. Data Protection
Solve issues such as low security of facial data and insufficient privacy protection.
4. Shared empowerment
Solve the problem of data loss traceability and inability to effectively achieve shared empowerment.
Unified facial platform
How to solve the problem?
1. Collection process
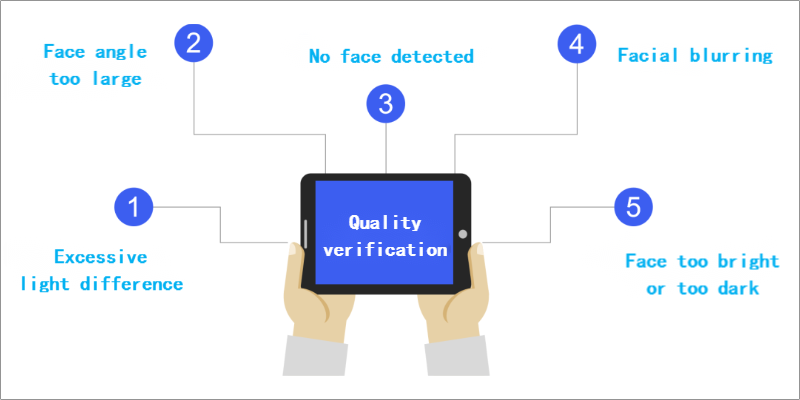
Build three-dimensional collection methods such as online and offline, self-service, and assistance, making it convenient for teachers and students to operate. Establish privacy protection agreement signing, image quality verification and evaluation, and self verification of personal similarity during the collection process.
2. Storage process
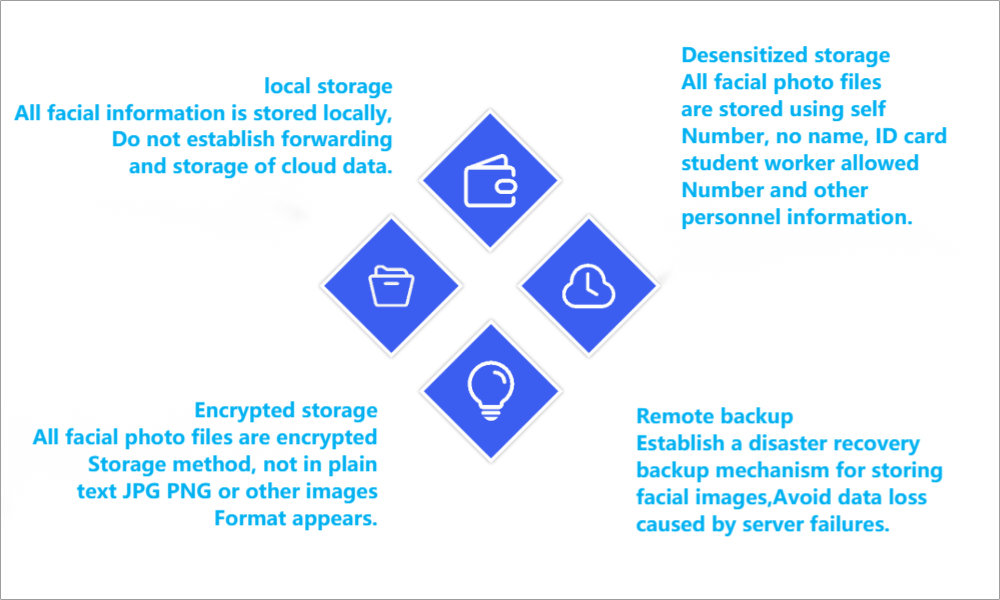
Encrypted storage of server image files, construction of remote backup method, fusion extraction of multi version facial feature values, recognition of terminal feature value model storage, to avoid photo leakage.
3. Transmission communication link
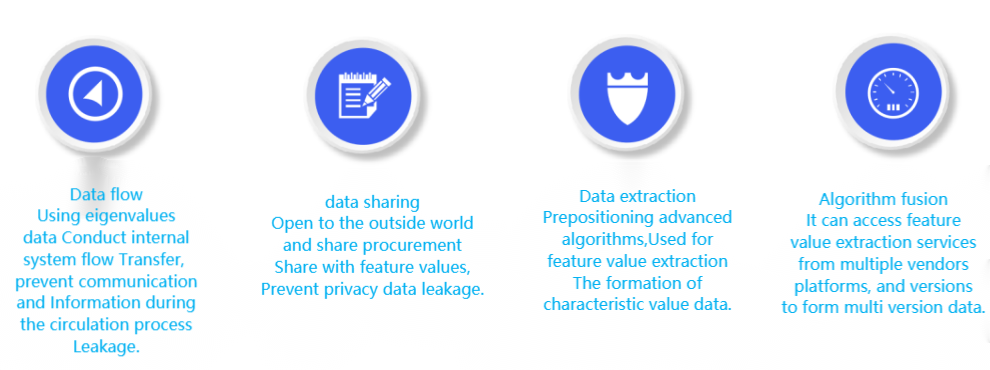
Adopting eigenvalue model for data communication to enhance data security during the communication process.
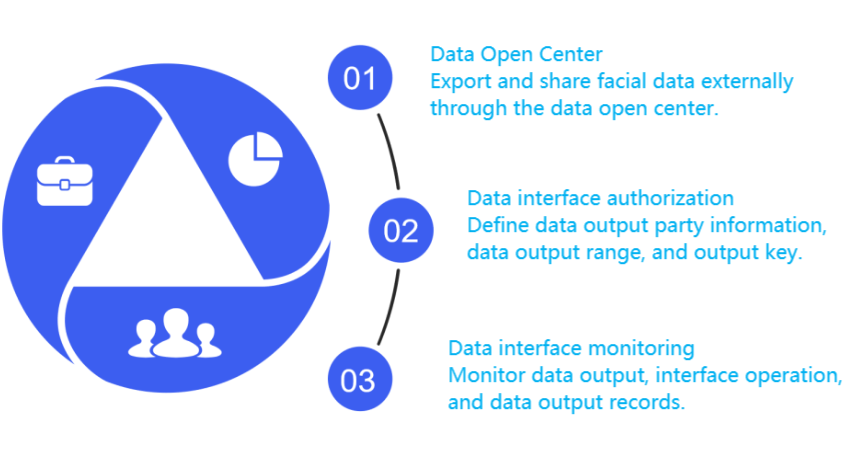
4. Shared empowerment process
Open fusion of multi version feature values, image sharing and loss tracing, establishment of sharing order, open security, and loss tracing.
Shandong will Data Co., Ltd
Created in 1997
Listing time: 2015 (New Third Board stock code 833552)
Enterprise Qualification: National High tech Enterprise, Double Software Certification Enterprise, Famous Brand Enterprise, Shandong Province Gazelle Enterprise, Shandong Province Excellent Software Enterprise, Shandong Province Specialized, Refined, and New Small and Medium sized Enterprise, Shandong Province Enterprise Technology Center, Shandong Province Invisible Champion Enterprise
Enterprise scale: The company has over 150 employees, 80 research and development personnel, and more than 30 specially hired experts
Core competencies: software technology research and development, hardware development capabilities, and the ability to meet personalized product development and landing services